Mitigate Ransomware Across All Locations with Cloud File Storage
June 18, 2020 | Tom Rose
As COVID-19 continues to spread, and users spend more hours working online, it should come as no surprise that malware authors are trying to exploit the pandemic. Weaker controls at home, and more users clicking on COVID-19-themed ransomware “lure” emails due to heightened levels of anxiety, are combining to create fertile ground for attackers. This is where cloud file storage platforms come in.
Previous Nasuni blogs summarized both the business impact of ransomware to organizations, as well as why traditional enterprise backup approaches that rely on centralized media servers quickly become a bottleneck when trying to mitigate ransomware attacks across many locations.
In this blog, we’ll drill down into Nasuni’s ransomware solution, and look at how Nasuni’s cloud architecture thwarts ransomware designed to target both production file storage and backup file infrastructure. By the end, you should understand the benefits of having a cloud file storage platform built around an infinite, immutable, versioned file system. And how such a file system can protect enterprises from ransomware attacks in ways that legacy file backup cannot, providing RPOs of minutes, even across many locations.
How to Mitigate Ransomware Across All Locations with Nasuni
Nasuni’s complete ransomware solution goes well beyond simple detection. Here is how Nasuni can help ensure that your organization can quickly mitigate ransomware across even a multi-petabyte global file infrastructure.
#1 Reduce the Ransomware Attack Surface
Nasuni customers reduce their ransomware exposure by consolidating all components of enterprise file infrastructure – NAS, file servers, backup, archive, and disaster recovery – in one cloud-scale platform that leverages the unlimited capacity and durability of Azure Blob, Amazon S3, Google Cloud Storage, and other cloud object storage platforms.
#2 Eliminate Backup from Becoming a Ransomware Target
The typical behavior of ransomware was to create a new encrypted version of each file, and then to delete the original file. Ransomware authors have now evolved their approach, and are no longer attacking just the production file storage environment, but are also targeting backup data and infrastructure as well, in an attempt to take out the “insurance policy.”
Nasuni Continuous File Versioning® replaces legacy backup, eliminating this attack point. With this next-generation snapshot technology, all file changes in all locations are de-duplicated, compressed, and stored as immutable, read-only objects in cloud storage, creating an infinite version history of the entire file system. As a result, you always have the last unaffected version of every file, from before the ransomware attack began. This enables you to restore all files, and resume operations, regardless of when the ransomware attack occurred or how much damage it did.
Nasuni customers can configure snapshots as often as every few minutes, which:
- Shortens the time between snapshots, so that there are fewer changes between the last “safe” version of a file and the infected version of a file.
- Allows for more granular recovery of files (RPO), so that you can choose from more recovery points after a ransomware attack.
#3 Audit Changes to Zero in on Ransomware Infections
Nasuni’s built-in file system auditing enables you to use the audit trail to selectively restore only those files that were infected by the ransomware. You can choose to audit Create, Delete, Rename, Write, and Security events for every volume. These events capture the typical behavior of ransomware, which is to create a new encrypted version of each file, and then delete the original file. Auditing these events will provide a record of which files were compromised and need to be restored, making surgical recoveries easier.
#4 Test the Ransomware Recovery Procedure
Periodically testing ransomware recovery procedures by simulating a ransomware attack can sharpen your response, help administrators become familiar with mitigation procedures, identify the best procedures to follow, and raise awareness of the threat posed by attacks.
Nasuni customers often follow these steps:
-
-
-
-
- Notify administrators and users that you are testing the process to recover from a simulated ransomware attack.
- Create a simulated threat. You can do this using a harmless test piece of simulated malware:
- Create an ordinary text file on a user’s computer. Make sure that this text file is included in a snapshot. This text file represents a file that becomes infected.
- The European Institute for Computer Anti-Virus Research (EICAR) provides harmless files that can be used for testing purposes. You can download the EICAR files from their site here.
- Replace the text file created above with the EICAR test text file. Make sure that this file is included in a snapshot. This file now simulates a file that has become infected.
- Perform recovery procedure to restore the original text file, before it was replaced by the simulated infected file.
- Record the steps that were performed. Then, examine these steps to determine which were most helpful in recovering from the simulated ransomware attack.
-
-
-
#5 Restore Safe Versions of Infected Files in All Locations
The most important step after a ransomware attack is having the ability to quickly recover compromised data. Nasuni is unique in its ability to enable you to locate and restore safe versions of infected files across your entire global file data footprint. This is due to two innovations:
-
-
-
-
- Unlimited Scalability – The Nasuni cloud file storage platform is designed around our UniFS® global file system, the only file system designed to reside and scale within limitless cloud object storage. Freed from the constraints of legacy hardware-based file systems, UniFS has no limits on the number or size of volumes, shares, files, or snapshots. With infinite snapshots and recovery points to choose from, you can select the one that is time-stamped just before the ransomware attack occurred.
- Multi-Site File Synchronization – Nasuni’s cache-from-cloud architecture, in which copies of only the frequently accessed files are cached from cloud storage on lightweight edge appliance virtual machines for high-performance access, enables ransomware to be eradicated in all locations. Once a “safe” version of a file is restored, it will be automatically synchronized to all locations that are caching the same file.
-
-
-
Whether you need to restore an entire volume, an individual directory (share), or individual files, Nasuni’s web-based management console makes recovering safe versions of files easy.
-
-
-
-
- Access the File System Browser.
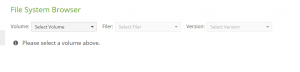
- Select the Volume containing files to restore.
- Select the Folder containing files to restore (this might be the root of the volume).
- For single files, select the file to restore. You can search by name.
- Select the Version of the specified files to restore. The version usually precedes the known time of the ransomware attack. You can search by date.
- Specify the destination of the restored files. Ideally, you are restoring files to their original location.
- Click Restore Folder or Restore File.
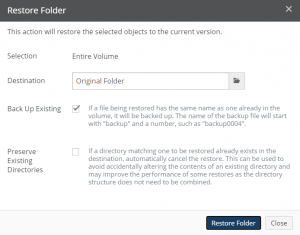
- Access the File System Browser.
-
-
-
Ransomware Recovery with Cloud File Services
Ransomware is now a common, everyday threat that must be dealt with by home computer users — and the largest enterprises. While mitigating ransomware at petabyte scale across all locations may seem daunting, Nasuni offers a modern cloud file storage platform that is proven to be an effective, comprehensive solution against ransomware attacks.
10/5/2020: This blog has been updated and republished under the title 4 Critical Steps for Fast Ransomware Recovery
Nasuni Customer John Shaffer shares the top reasons that Greenhill relies on the Nasuni hybrid cloud storage platform and more in his guest blog post.
Jim Liddle shares how innovations in machine learning and AI are helping enterprises get Fit for AI through intelligent automation.
Russ Kennedy walks enterprises through how they can set their data and infrastructure up for success by being AI ready.


